What Does Zero Trust Mean?
Zero Trust (ZT) is a data-centric cybersecurity strategy for enterprise computing that assumes no end-user, computing device, web service, or network connection can be trusted — even when an access request originates from within the organization’s own network perimeter.
The Zero Trust model has evolved to take into account distributed computing and an ever-expanding attack surface. Unlike a single sign-on (SSO) strategy that allows users to log in once and access multiple network services without re-entering authentication factors, Zero Trust requires authentication factors to be verified — and re-verified — each time a network resource is requested.
Because untrusted threat actors exist both internally and external to a network, Zero Trust supports the following principles:
- Never Trust
- Always Verify
- Enforce Least Privilege
An important goal of the Zero Trust Model is to prevent malicious actors from using a compromised account to move laterally across a target network.
Techopedia Explains Zero Trust
In the past, cybersecurity efforts were focused on protecting the network perimeter. With the growth of the distributed cloud and edge computing, network elements that historically weren’t a part of access control decisions have become essential — and need to be protected just like any other attack surface.
How Zero Trust works
Zero Trust protects critical data and resources both inside and outside the traditional network perimeter by using information gathered in real-time from multiple sources. This requires DevOps teams and security engineers to work together and design an integrated set of security processes capable of inspecting and logging all types of network traffic.
Zero Trust Network Access (ZTNA) uses the principle of least privilege (POLP) to limit access to network resources. ZT Identity and Access Management (IAM) processes rely on a combination of contextual factors, including username, password, device type, IP address, and physical location to decide whether an access request should be allowed or denied.
Microsegmentation is playing an important role in Zero Trust because it logically breaks a large network into smaller, more manageable segments. Dividing the network into microsegments allows network security engineers to detect and contain intrusions significantly faster and more effectively than is possible with traditional, monolithic cybersecurity architectures that are only designed to protect the network perimeter.
A Zero Trust architecture requires a robust cybersecurity infrastructure capable of making, logging, and enforcing access decisions for disparate (but related) cybersecurity capabilities. Network and engineers will need to know how to use software-defined networking (SDN) and machine learning (ML) algorithms to look for data patterns that indicate malicious activity in real-time. To ensure access control enforcement remains as granular as possible, security engineers will also need to know how to work with artificial intelligence (AI) and the robotic process automation (RPA) programming that will grant or deny access permissions.
As IT teams transition towards optimal zero trust implementations, there is an increased reliance on using automated processes and systems to enforce security policies.
Zero Trust Challenges and Advantages
Zero Trust implementation is not easy. Moving to a Zero Trust security model requires everyone in an organization to understand and commit to the need for verification and re-verification requests.
At its best, a successful Zero Trust strategy will help ensure damage can be quickly contained and remediated when a particular user credential, hardware device, or network service is compromised. When implemented poorly on the back end, however, Zero Trust can cause latency and a poor user experience (UX).
Zero Trust vs. Risk-Based Authentication
A “risk-based authentication” scheme can be used to complement Zero Trust and reduce latency. Risk-based authentication allows security engineers to rank the resources they want to protect based on criteria such as the risk level associated with a specific user’s IP address.
Instead of NEVER trusting and ALWAYS verifying, an RBA approach can eliminate access controls for interactions that carry a low risk, but enforce Zero Trust for transactions that pose a higher level of risk. This hybrid version of Zero Trust may also be referred to as “Adaptive Authentication.”
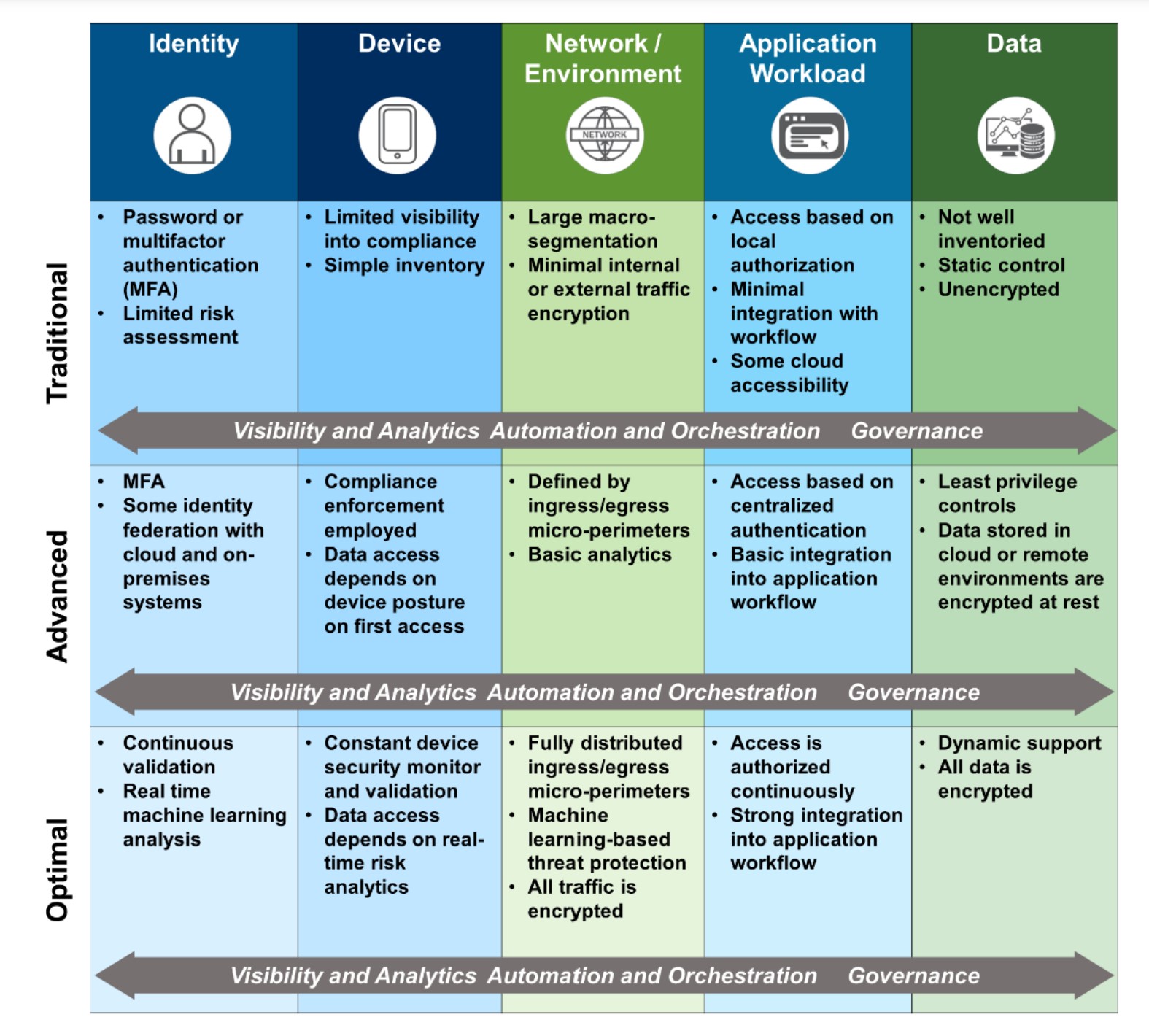
Zero Trust Maturity Model
The Zero Trust Maturity Model provides a framework to help businesses understand how close they are to fully implementing and optimizing a Zero Trust Architecture. A maturity model is a type of analytical tool that provides a framework for assessing how close a business initiative is to meeting a desired set of core principles and standards.
The Zero Trust Maturity Model can be used to evaluate progress towards five criteria referred to as pillars:
Identity – How well does a Zero Trust implementation use a combination of factors to validate and continuously verify an identity throughout the duration of the identity’s interactions with services or data?
Device – How effective is a Zero Trust implementation when it comes to assessing the integrity of networked computing devices by providing security protections and visibility into the devices themselves?
Network – How closely does a Zero Trust implementation align network segmentation and protections with the needs of application workflows?
Application Workload – How effectively does a Zero Trust Architecture apply zero trust principles to the development and deployment of software applications by using continuous integration and continuous deployment to integrate security testing and verification into each step of the development process?
Data – To what extent does the Zero Trust implementation use a data-centric approach to cybersecurity that requires IT staff to identify, categorize and inventory data assets so they can prioritize data protection for their most critical data assets?
History of Zero Trust
While the term Zero Trust is often credited to John Kindervag, some security experts credit Stephen Paul Marsh with coining the term.
A report published by Forrester research analyst, Dr. Chase Cunningham, entitled, “The Zero Trust eXtended (ZTX) Ecosystem Report” delves further and outlines how an eXtended Zero Trust framework can support networks, data, workloads, devices and people.