What is 256-Bit Encryption?
256-bit encryption is a data/file encryption technique that uses a 256-bit key to encrypt and decrypt data or files.
256-bit encryption refers to the length of the encryption key used to encrypt a data stream or file. An encryption key is a string of binary digits (bits) that determine the output of a cryptographic algorithm. A hacker or threat actor will require 2256 different combinations to break a 256-bit encrypted message, which is virtually impossible to be broken by even the fastest computers.
It is one of the most secure encryption methods after 128– and 192-bit encryption and is used in most modern encryption algorithms, protocols, and technologies, including Advanced Encryption Standard (AES) and Secure Sockets Layer (SSL). It is commonly used in online banking, VPNs used for streaming, SSL/TLS for websites, and many other applications requiring data privacy employ high encryption techniques.
Typically, 256-bit encryption is used for data in transit or data traveling over a network or Internet connection. However, it is also implemented for sensitive and important data such as financial, military, or government-owned data. In fact, the US government uses AES with 256-bit keys to secure classified information.
Key Takeaways
- Encryption converts data into a coded form to prevent unauthorized access.
- 256-bit encryption is one of the most secure encryption standards available today.
- It is often used for sensitive data such as financial, military, or government-owned data.
- Side-channel attacks that exploit physical leaks in encryption implementation are a security concern.
- Quantum computing may pose a future threat from advanced quantum algorithms.
How 256-Bit Encryption Works
Encryption converts data into a coded form to prevent unauthorized access. 256-bit encryption refers to the length of the encryption key.
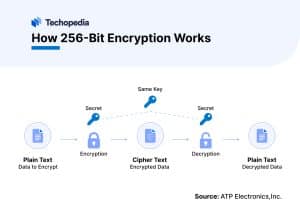
Here’s how it works:
Key generation
A 256-bit key is created, consisting of 256 binary digits, resulting in 2256 possible keys.Encryption algorithm
This key is used by an algorithm, like AES, to transform plaintext into ciphertext.Decryption
The same key, or a corresponding private key in asymmetric encryption, is used to revert the ciphertext back to plaintext.
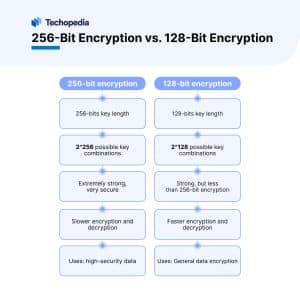
256-Bit Encryption vs. 128-Bit Encryption
Uses of 256-Bit Encryption
256-bit encryption is widely used for securing sensitive data, providing a high level of protection across various applications.
Examples include:
256-Bit Encryption Pros and Cons
Pros
- Compatible with most modern systems
- Follows established encryption standards
- Secure against brute-force attacks
- Suitable for various applications
Cons
- Harder to implement correctly
- May not work with older systems
- Requires more computational power
- Slower than 128-bit encryption
256-Bit Encryption Security
While 256-bit encryption is extremely secure, there are potential security risks associated with its use.
Examples include:
- Encryption backdoors create hidden access points in encryption software.
- Human factors include user errors and social engineering vulnerabilities.
- Implementation errors are bugs or flaws in encryption algorithms.
- Key management involves securely generating, storing, and distributing encryption keys.
- Quantum computing may pose a future threat from advanced quantum algorithms.
- Side-channel attacks exploit physical leaks in encryption implementation.
Can You Break 256-Bit Encryption?
The 256-bit encryption definition refers to the length of the encryption key, which is 256 bits long. It is one of the most secure encryption standards available today, even against brute-force attacks where an attacker tries every possible key combination. Breaking 256-bit encryption would take an unimaginable amount of time, even with the fastest computers.
The Bottom Line
The 256-bit encryption meaning is a data/file encryption technique that uses a 256-bit key to encrypt and decrypt data or files. It is one of the most secure and widely used methods for securing sensitive data, providing a high level of protection even against brute-force attacks.
However, potential risks and challenges include implementation errors, improper key management and side-channel attacks. While 256-bit encryption is recommended for sensitive data, 128-bit encryption may suffice for less sensitive data, offering a good balance between security and performance.